Over the past year, we have detected multiple exit scams employing bots for wash trading, a deceptive practice designed to attract unsuspecting investors. These scammers employ a subtle yet effective technique, transferring funds across various tokens—a strategy that sometimes slips under the radar of security assessments and exit scam post-mortems. They utilize platforms like Disperse.app and CoinTool, which enable them to shuffle coins between bot-operated addresses that acquire the scam tokens. Subsequently, the scam's initiator, or an associated address, extracts all liquidity, resetting the scheme. In this article, we will dissect this method, explore the scammers' likely objectives, and delve into the potential implications for money laundering. This piece aims to increase security researchers' awareness of this technique in order to assist with research.

The Method
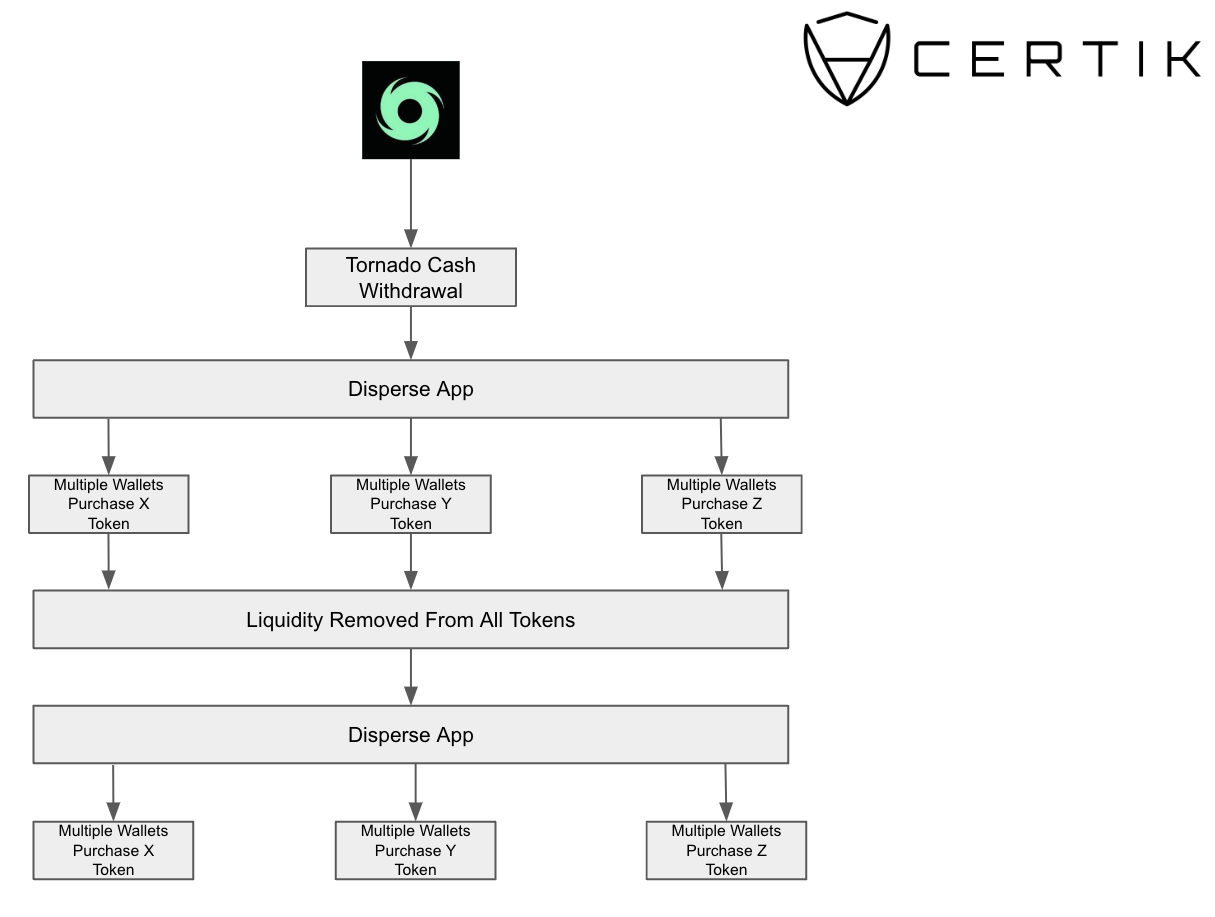
We’ve uncovered a series of complex maneuvers involving token transactions, initially suspected to be part of extensive exit scams. However, a deeper look reveals more intricate activity. Instead of a large victim base, many purchasing wallets were traced back to funds distributed by a wallet connected to fraudulent activities, utilizing multi-send platforms like Disperse.app. Such tools enable the distribution of digital assets to numerous addresses in a singular operation.
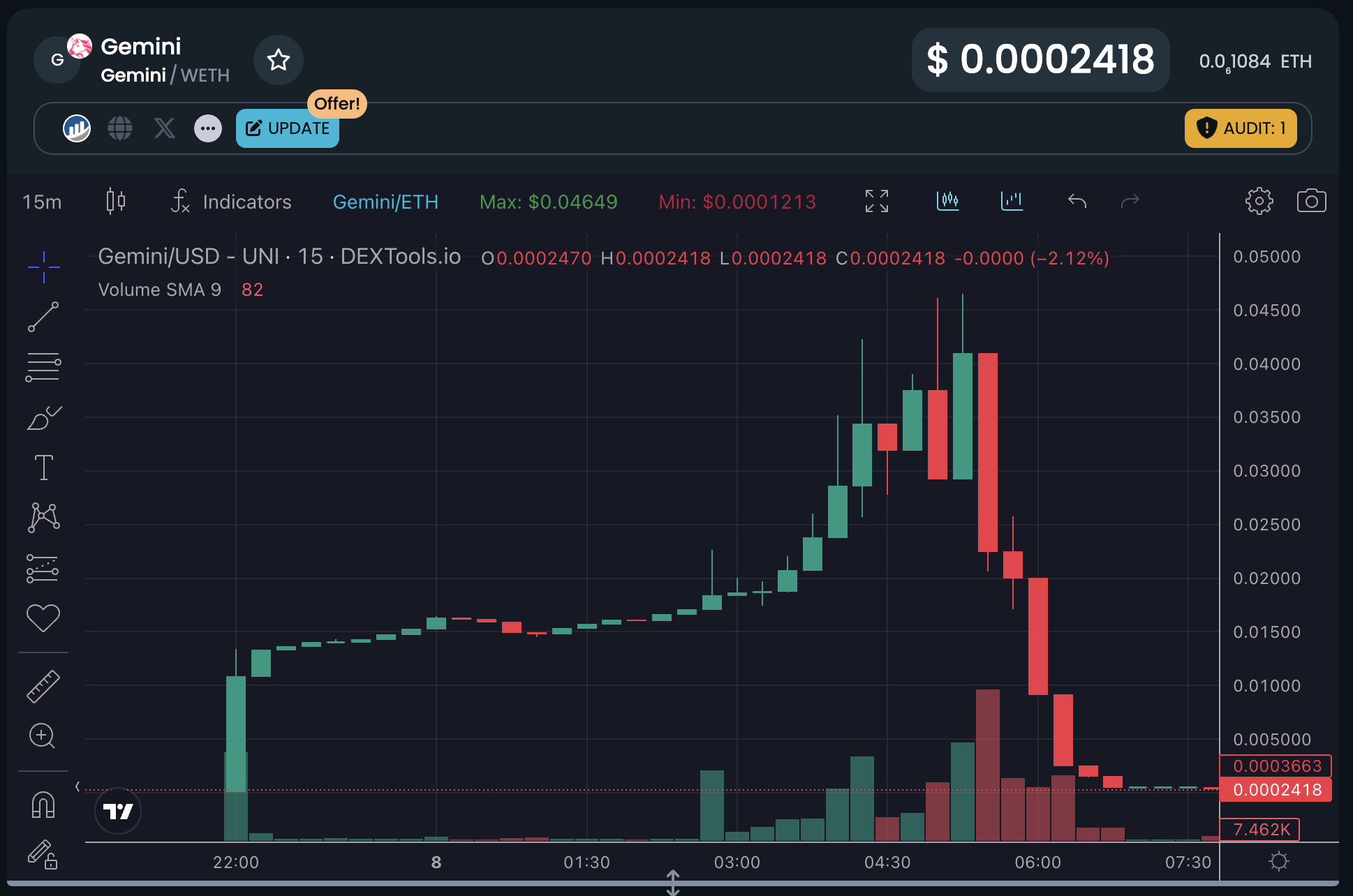
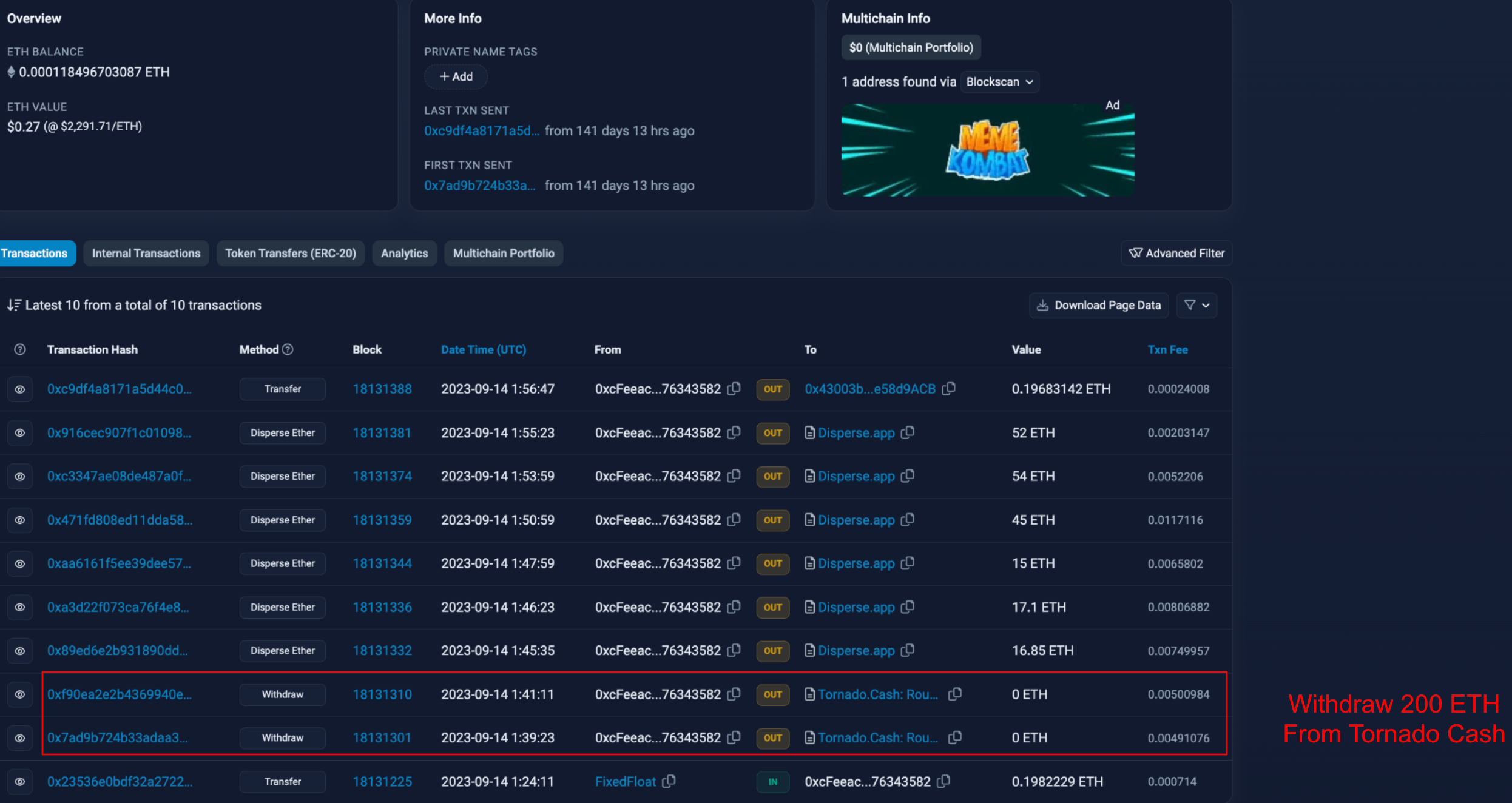
We have identified this pattern of behavior on both Ethereum and BNB Chain, with every likelihood that similar schemes are underway on other networks too. The typical pattern observed involves substantial withdrawals from Tornado Cash to a designated wallet (Wallet A). Concurrently, another wallet (Wallet B), also funded via Tornado Cash, proceeds to create an ERC-20 token and then adds liquidity to the market. Subsequently, Wallet A channels funds to various addresses, which in turn acquire the token established by Wallet B. After a predetermined interval, Wallet B, or an affiliate, extracts the liquidity from the market, reallocating the funds into fresh wallets, thereby setting the stage for the cycle to be repeated.
The Goal
The likely goal of these scammers is to deceive a small number of people into buying their fake tokens. After a few unsuspecting individuals have made purchases, the scammer withdraws all the invested money and uses it to artificially inflate the value of another token. Typically, there are several fake tokens in circulation simultaneously, allowing the scammers to operate on a large scale and accumulate significant losses across different tokens.
We assess that the scammers aim to create false demand to trick automated trading bots on platforms like X and Telegram. They continue this scheme until they've siphoned a certain amount of real money or until the token's trading activity declines. At that point, the scammer drains all the funds from the token's liquidity pool and proceeds to launch a new scam token.
Below are a few examples of these types of tokens:
Fake Gemini: 0xF716380d87b9f9d25Ba749E1735Ca8b1E0E3b392
GROKAI: 0xd403F941FFD6ff30d139B97526ff655E5142ed21
Mooon Token: 0xfac14acc884840130876e9e047a2c5c7f9be0018
XDoge: 0x064f4A422CC15773f5CE246F278ff090F2075C14
These fraudulent tokens often activate certain X bots, leading to automated posts that include details like the token's market cap. Below shows the automated posts of the above contracts.
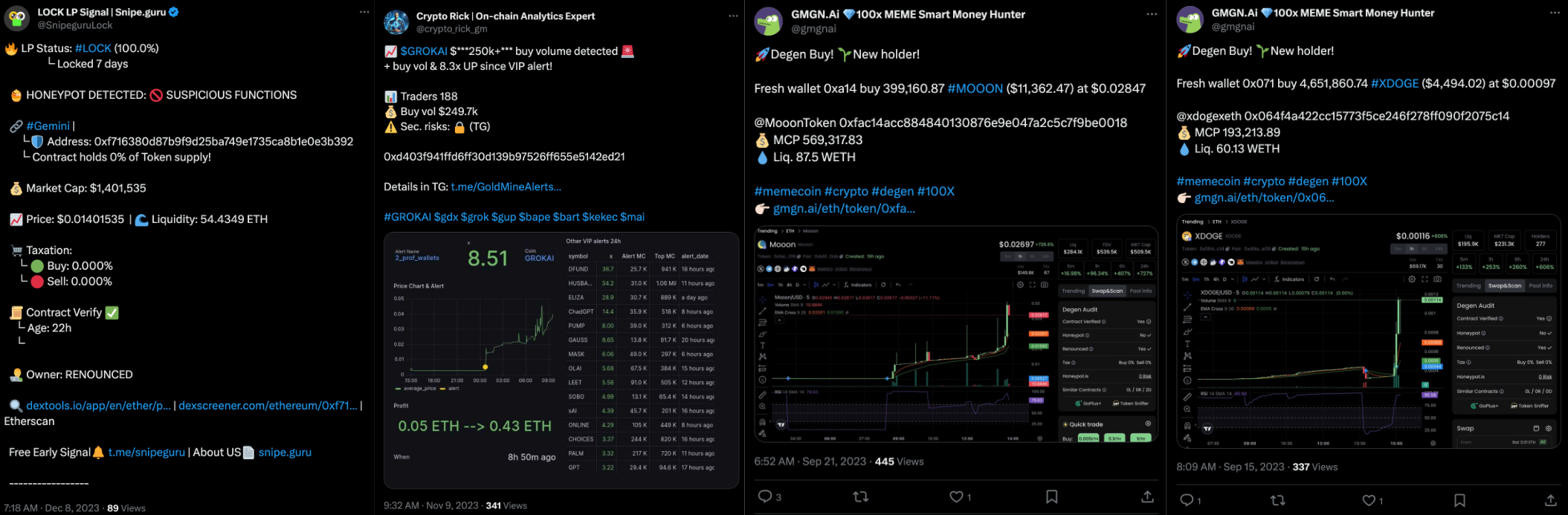
The scammers take only basic steps to make these tokens look real at first glance, such as setting up an X account, creating a Telegram channel, and designing a simple website. Notably, these websites typically show nothing more than the token's contract address and a logo, and the X accounts usually have very few followers.
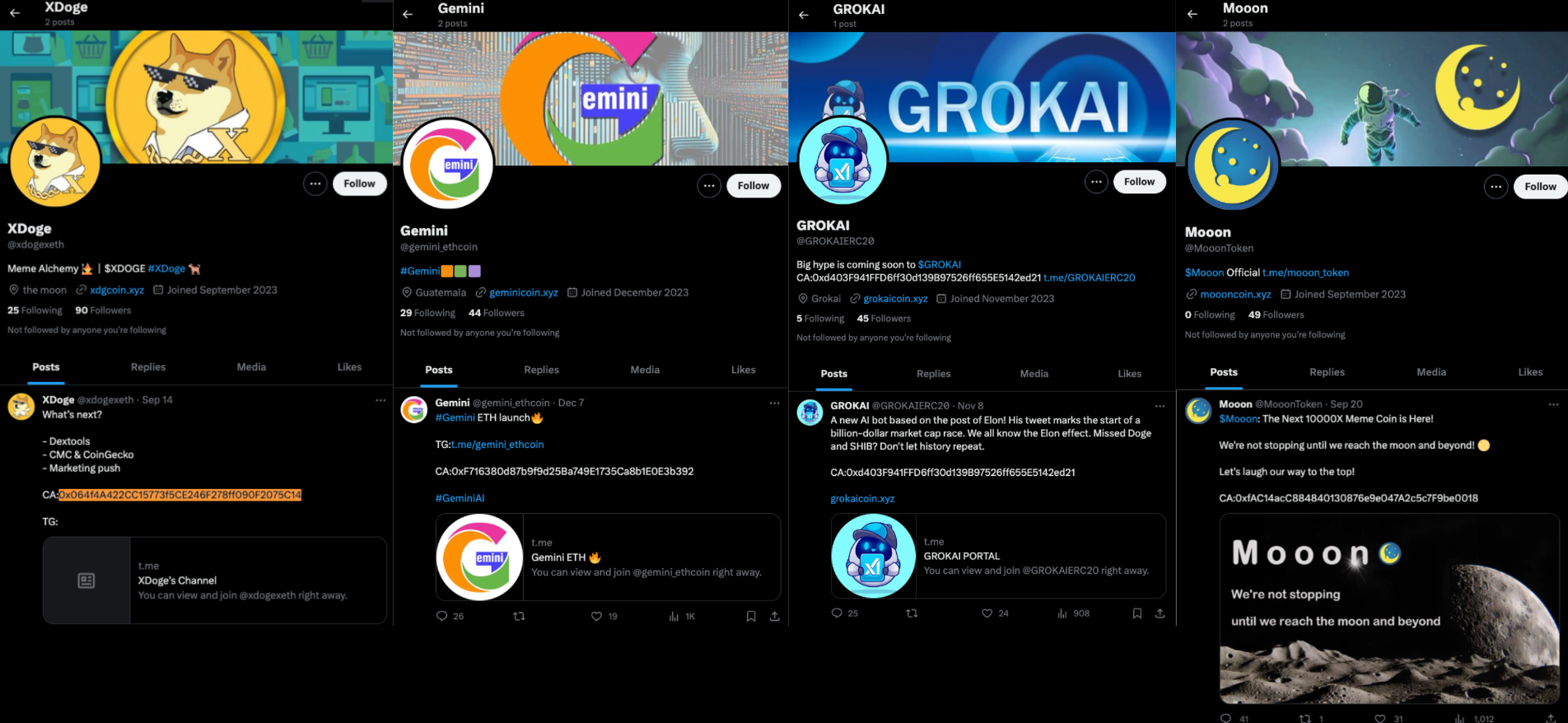
The websites also exhibit a clear pattern. Below are the screenshots of three of the websites of three of the tokens.

A common thread among these scams is that their website's main IP address is often located in Singapore, based on data from URLscan.
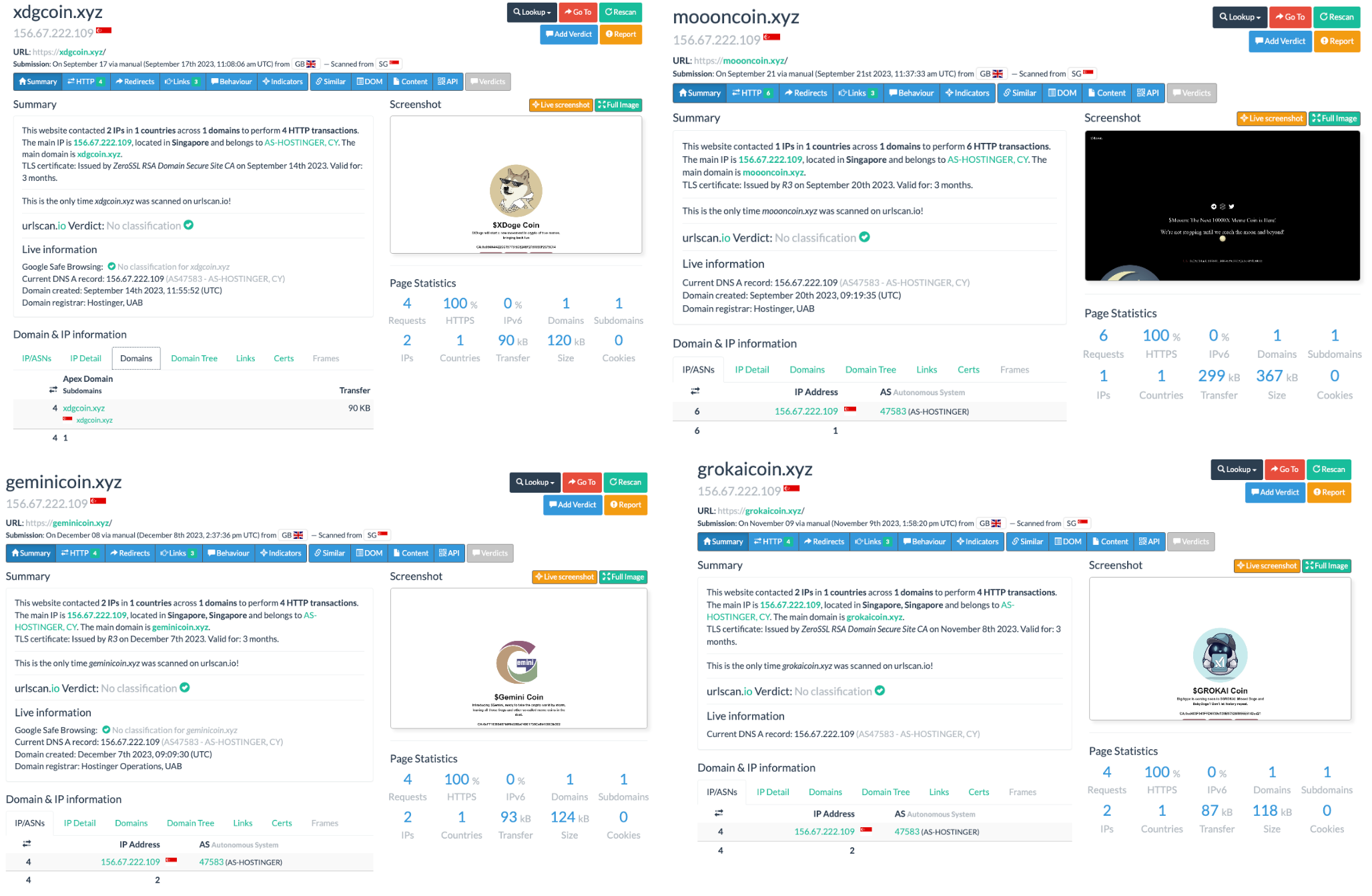
Our analysis indicates that the high volume of fake transactions (wash trades) is designed to activate bots that track new token launches. When victims check out the token contract based on these bot alerts, they find a social media profile and a website, which might convince some to invest in the token.
After cycling funds through several fake tokens, the scammers typically launder the money through services like Tornado Cash, repeating a pattern similar to activities we observed in August 2023.
A Money Laundering Technique?
Such a technique possibly has a money laundering application too, as funds withdrawn from mixers such as Tornado Cash are cycled through multiple tokens. It's critical to note that during investigations into such scenarios, the background activities of the so-called “victims” might go unchecked. This oversight occurs when transactions are prematurely classified as exit scams.
Money laundering through fake tokens isn’t a new phenomenon. Consider, for instance, a token named SolarCity (0xbe6a24Bb6358bc8ec7744F5ff8BD04514598298B) from 2022, which we identify as exhibiting signs of money laundering. The operation typically follows this sequence:
-
The deployer initiates a new token.
-
Associated wallets acquire the token.
-
The deployer withdraws all liquidity, redistributing funds across various wallets.
-
A subsequent token is launched and funded using assets from the initial token.
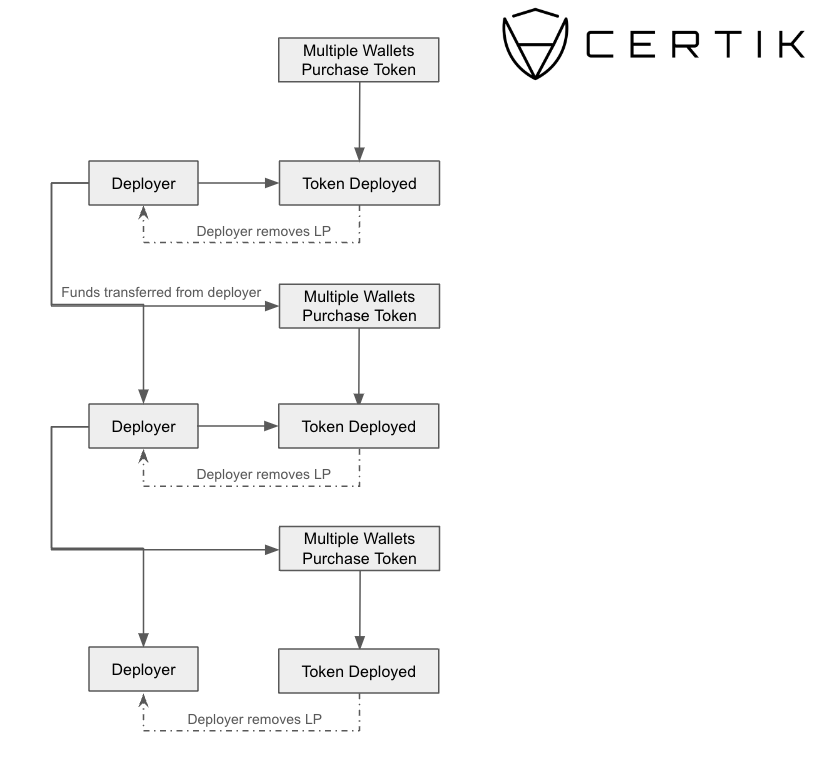
This cycle, often automated, can be repeated indefinitely.
The example above showcases historical methods of potential money laundering via tokens. However, this strategy might also apply to the tokens under discussion in this analysis. The misunderstanding that these tokens result from exit scams—sometimes reflecting losses upwards of $100,000—leads investigators to overlook the origins of the funds. This assumption could mislead them into believing that the majority of the funds originate from victims, hence deeming a deeper investigation unnecessary.
In examining the origins of the funds associated with the tokens mentioned earlier, it's observed that the initial wallet typically has withdrawn significant amounts from Tornado Cash before distributing ETH across various accounts. The deployment wallet for XDoge is connected to numerous wallets exhibiting patterns similar to those described. This pattern underscores the need for thorough investigation into the financial pathways of such tokens to uncover potential laundering activities.
Looking Deeper
A common trait among deployers of these scam tokens is that they are often initially funded through FixedFloat transactions. For instance, the deployer of the Mooon token received an incoming FixedFloat transaction likely sent from the external owned account (EOA) 0x5aE4E5fF97c2c0b4152fc75566fd7cFF039B2839 on the Arbitrum network. This wallet has several outbound transactions to FixedFloat deposit addresses, which are then likely transferred to other scam token deployers. This pattern suggests that a group may be utilizing Arbitrum network wallets to initially fund deployer wallets on the Ethereum network through FixedFloat.
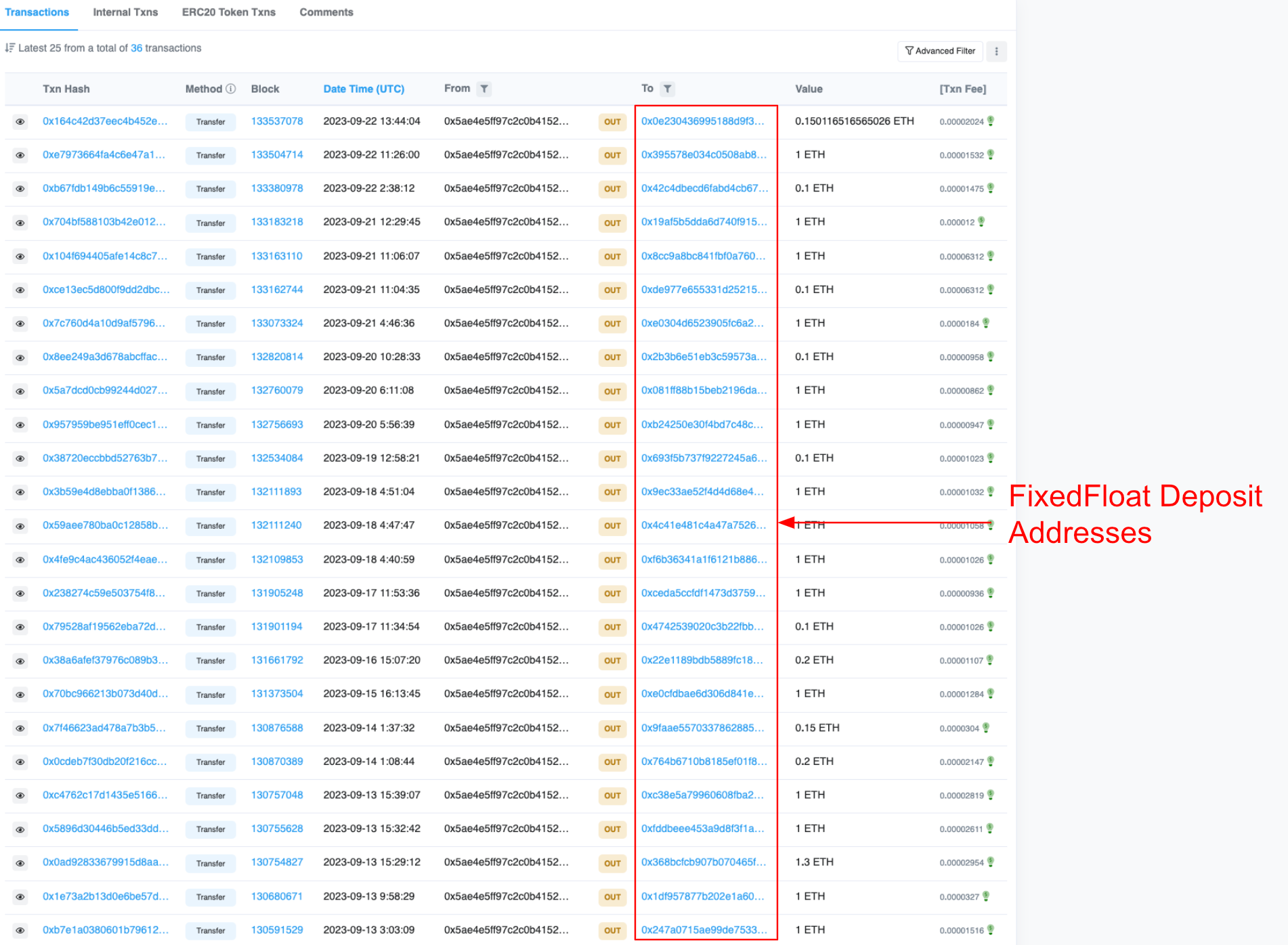
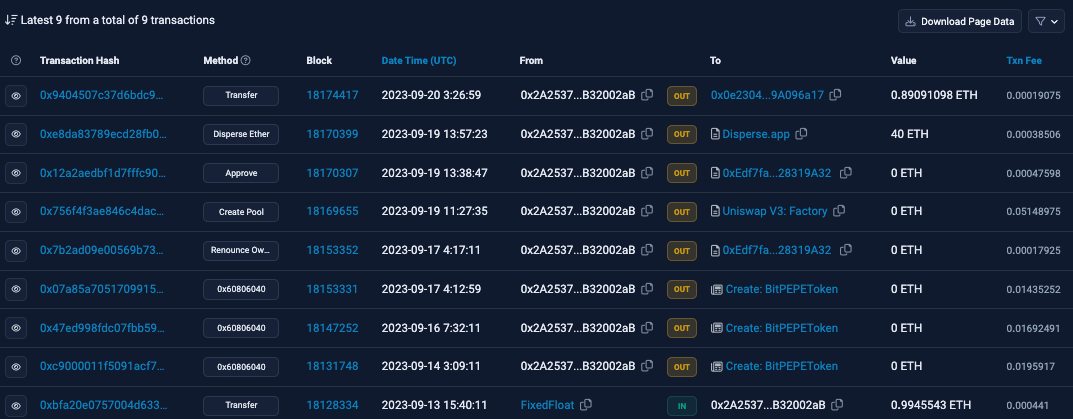
For example, examining a specific FixedFloat deposit reveals that the probable recipient wallet is 0x2A2537E9FC6bDb52D2627758E7ED79CBB32002aB, which subsequently created a scam token named BitPEPE.
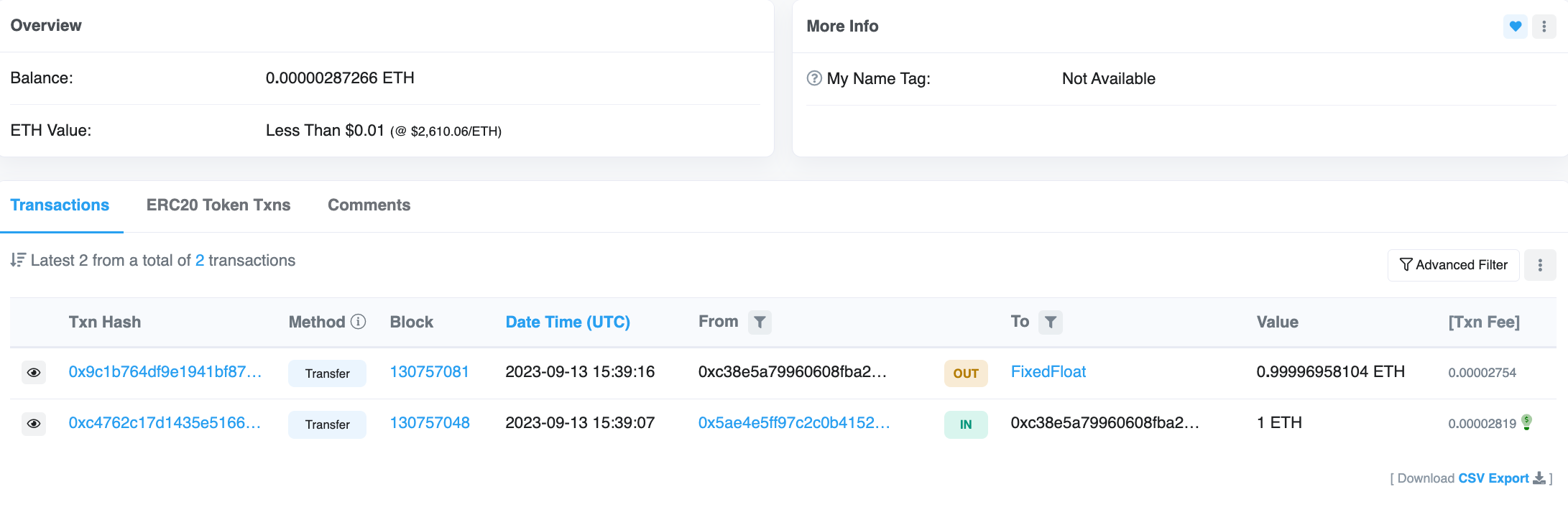
The ETH sent from address 0x5ae on Arbitrum originates from the same address on the Ethereum network. Analysis of the Ethereum address reveals similar activity as previously described, including transferring large sums of ETH via Disperse[.]app and interactions with scam tokens. Tracing back the incoming Disperse[.]app transactions, we find that the funds originated from several large withdrawals from MEXC on July 14, 2023. As of this writing, we have not been able to confidently identify the deposit transactions related to this group.
Examples On Other Chains
Similar patterns have been observed on other blockchain networks. A notable instance involved a token fittingly named "Rug.” The distinctive feature here was the deployment of a contract by the scammer's address to distribute BNB, as detailed in the transaction below:
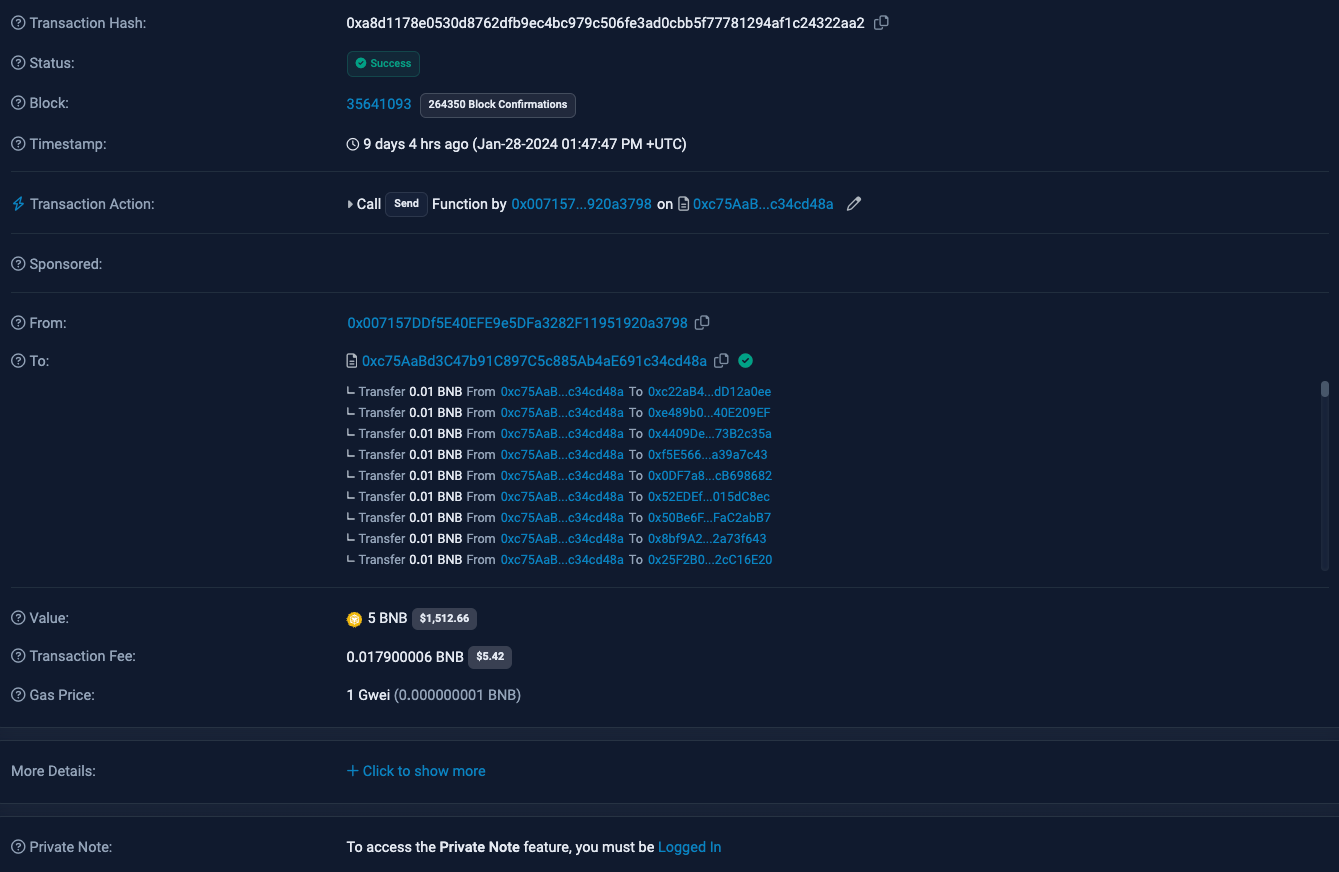
The wallet initiating the send was initially funded by the external owned account (EOA) 0x2b0335eF47047EDaf94F1DF794d65d2eF2412c46. Tracing the transaction history reveals an incoming USDT transaction from the Arbitrum Network via Stargate.
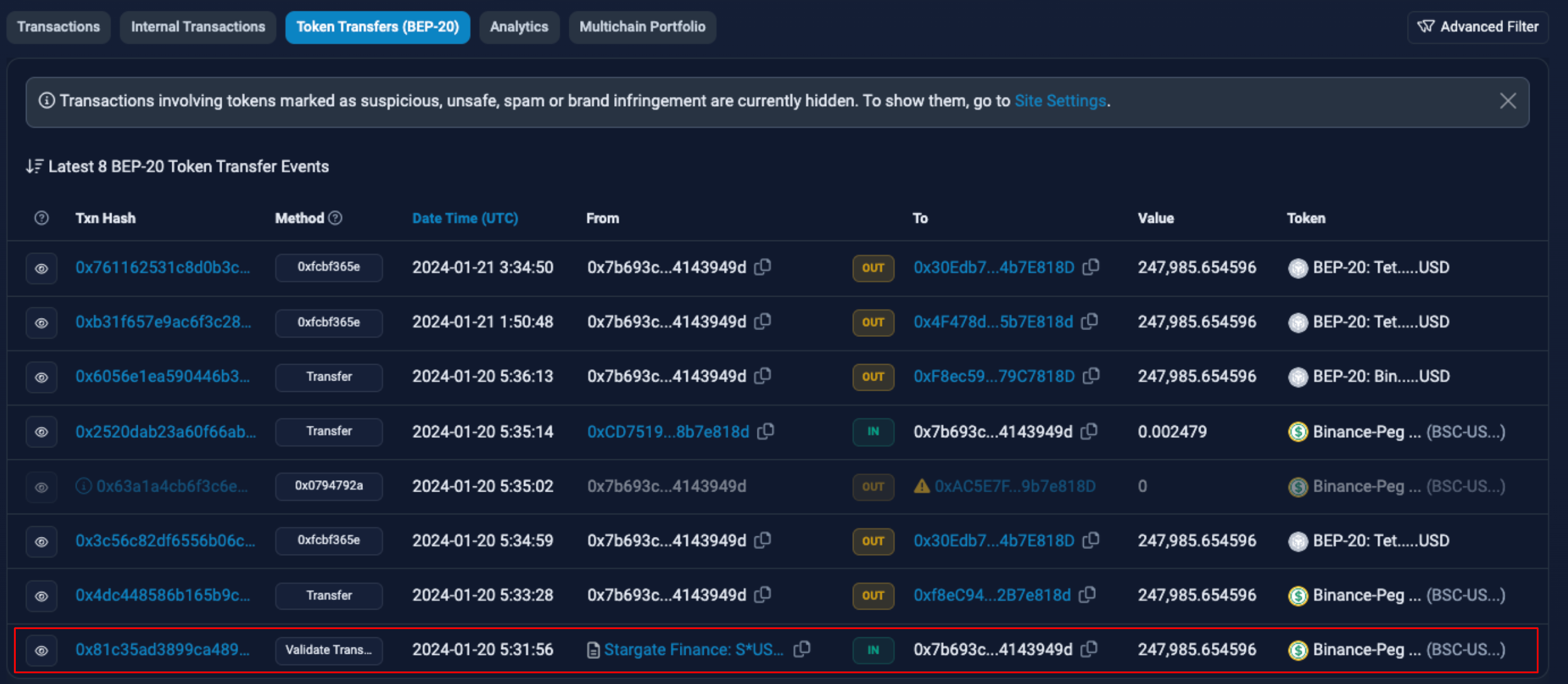
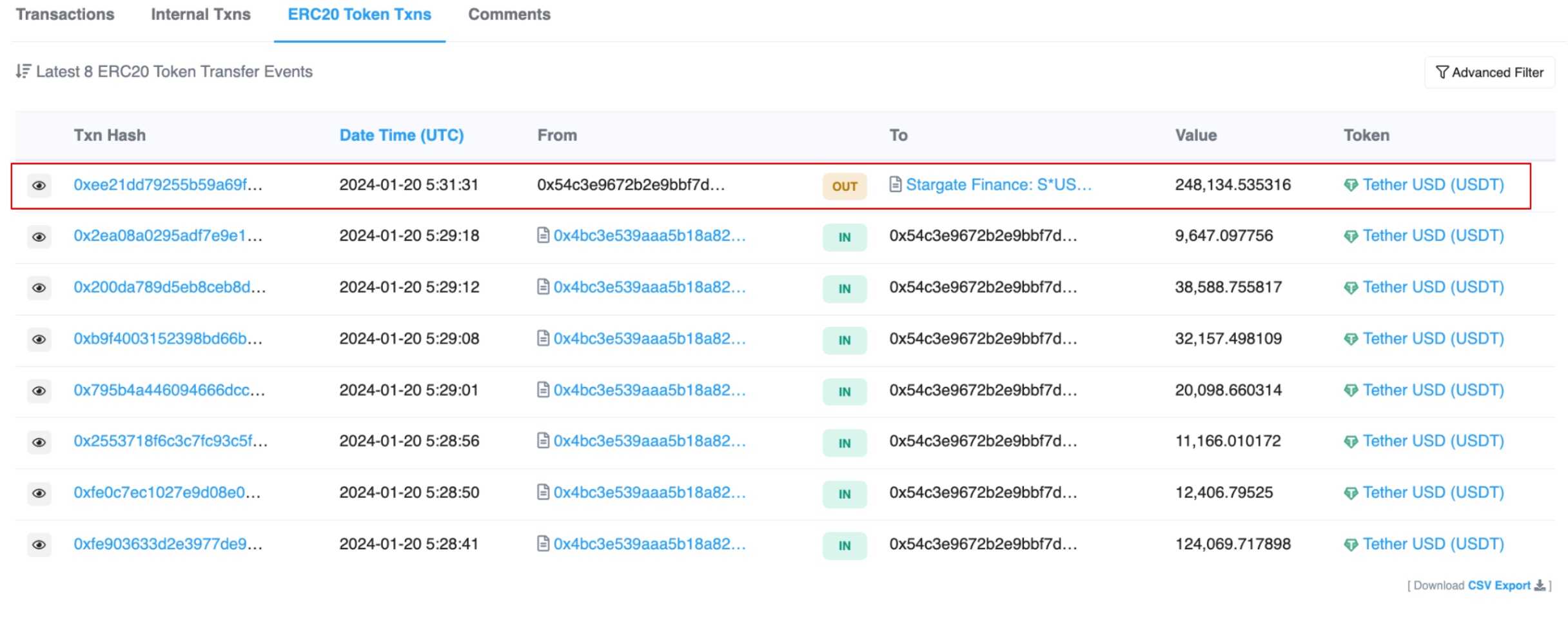
This USDT originally came from EOA 0x2231, which received 100 ETH from address 0xaFa. This ETH, in turn, traces back to a transaction initiated on Ethereum by EOA 0xe4b, connected to withdrawals from Tornado Cash.
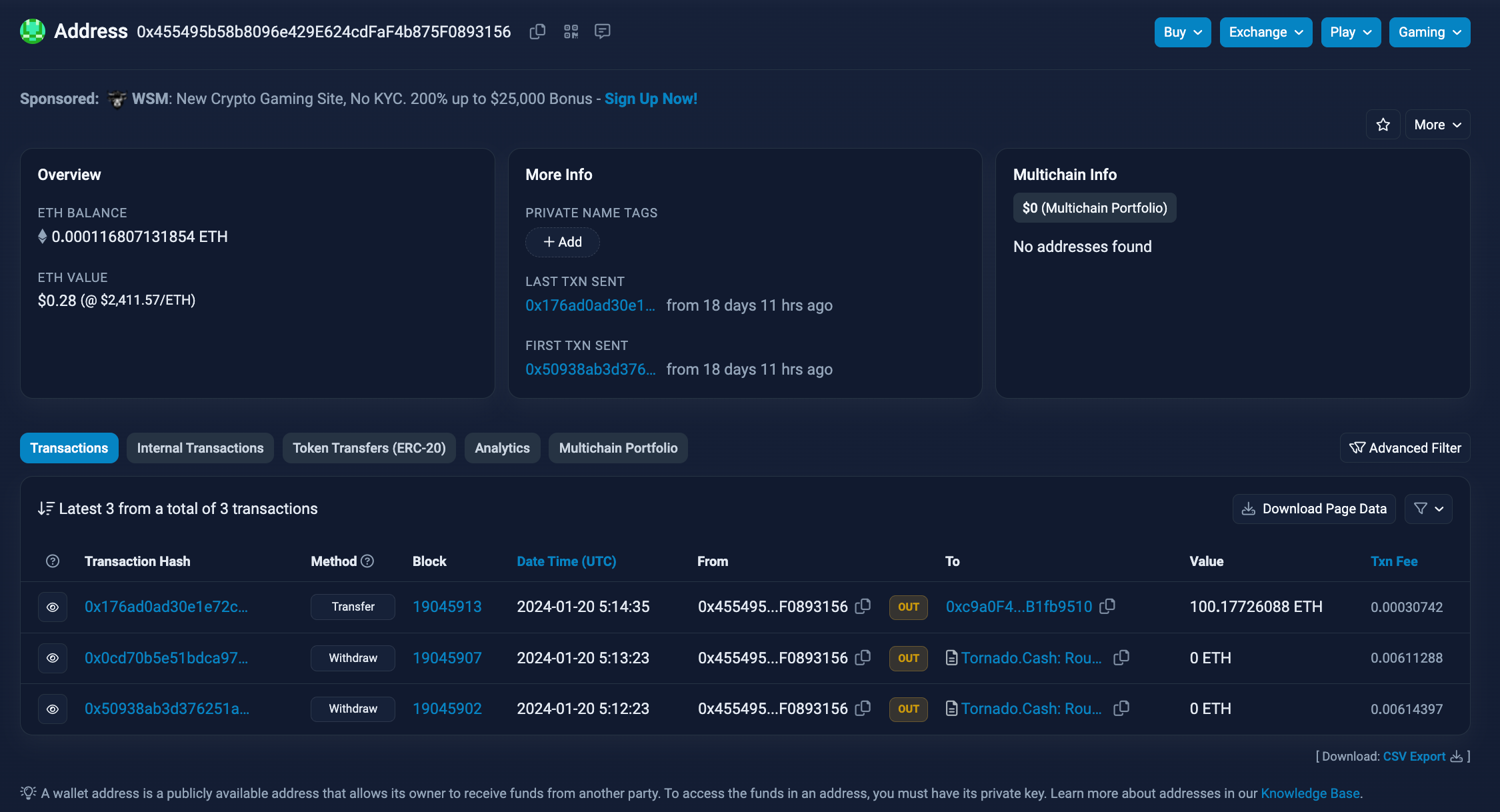
The origin of the Tornado Cash withdrawals remains uncertain; they may be tied to previous scam tokens or entirely unrelated activities. Nonetheless, this illustrates a systematic approach to dispersing funds across multiple wallets for the purpose of purchasing scam tokens.
Conclusion
While this analysis has primarily focused on the utilization of Disperse.app for transferring funds among bot accounts, enabling the artificial inflation of scam token trading volumes, other tools have also been used. While there may be aspects of money laundering given the transaction volume, the underlying intent appears to target funds from a limited group of investors per token. Investigators examining exit scams should note this tactic, as it aids in identifying non-genuine accounts, crucial for accurately evaluating the extent of losses incurred.



